In a previous article I did a high-level overview of what wireless site surveys are and what they are used for. In this article I'll dive in a little deeper to give some insight on what packet captures and RF Monitor-Mode are, are and what they can reveal.
There are two modes a wireless NIC can be in - connected/disconnected, and monitor-mode. Connected is exactly what it sounds like - the NIC is connected, or in 802.11 parlance, "Associated", to an access point. When a device is associated it can transmit/receive data through the AP. This is how most people experience Wi-Fi - associated to an AP, doing whatever it is they are doing - watching Netflix, sending an e-mail, upload a file to a server, etc.
Monitor-mode, or "RF" monitor-mode implies you are not associated/connected to the WLAN, so you are DISCONNECTED, but you are LISTENING, or "monitoring". This mode is often not simple to achieve. It requires the ability to manipulate the wireless driver to set the NIC into this mode. Monitor-mode allows the wireless NIC to listen to a specific channel, a set of channels, or ALL the channels in 2.4/5GHz.
Also, if you cannot place your NIC into monitor-mode you cannot see wireless frames. When you are associated/connected to a WLAN, all you can see are the upper layer data flow. This would include things like DHCP, IP addresses, DNS, webpages, etc. That may be fine if you are looking to troubleshoot something in the network, for YOUR device, but not so much if you are trying to troubleshoot a WIRELESS/802.11 problem in the AIR.
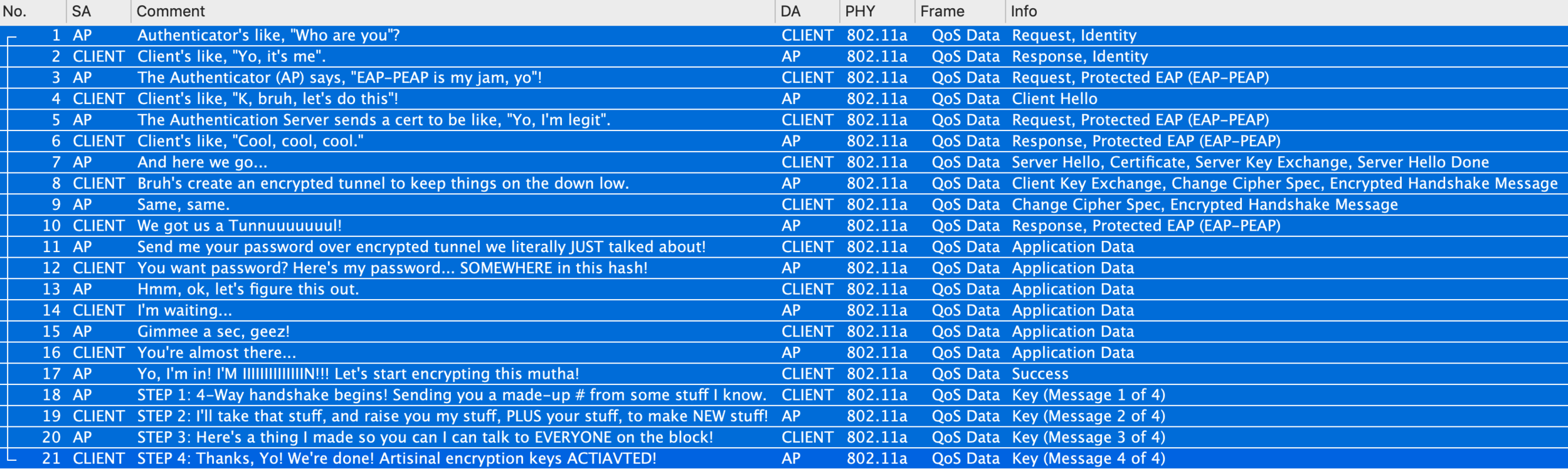
Everything I've highlighted so far is related to what we call wireless PACKET CAPTURE. The purpose of a packet capture is to "capture" all the data transpiring during the error you are troubleshooting. You can then review the data in your chosen packet analysis software and dig in to potentially discover the reason for the problem your device is experiencing.
The most common use-case for monitor-mode is to perform wireless packet captures. This can be difficult to achieve. You need specific hardware, and custom drivers, that allow the NIC to use this mode. For Windows, this is almost impossible with the built-in adapter. Mainly due to the fact that there is no standardized NIC that all Windows machine use, so you are often left with researching and purchasing a 3rd party adapter that can use monitor-mode. Even then, the adapter you may have limitations of what information it can actually present to you. So, you wind up purchasing and testing several adapters until you find the one that works best for you intended use.
For Windows, the best results can be found by using 3rd party software, and their recommended adapters. With limited success, Wireshark 3.0 and newer, will allow for monitor-mode captures with some adapters. I have a video on how to do this on YouTube. Commercial software such as MetaGeek Eye P.A., TamoSoft, CommView for WiFi, and LiveAction’s Omnipeek are popular and easier to implement.
On Linux and MacOS, things are a bit better. Specifically, macOS, since the NICs used are limited across the platform, and the OS is based of a UNIX variant, you can set the internal adapter to monitor-mode at will. This makes Macs a favorite among some wireless engineers, along with Linux, of course. One caveat, the new M1 MacBooks use a new 802.11ax adapter that does not render monitor-mode data correctly when capturing on 80MHz channels, so until that is resolved, only pre-M1 Macs are reliable for 80MHz captures.
So, Monitor-Mode is critical for doing in-depth 802.11 analysis. Like troubleshooting why a particular device, or application, is not performing as expected, or validating if that client, or application is functioning as expected.
I think of packet captures as more of a “micro-level” tool, as opposed to say a wireless site survey which is more of a “macro-level” tool. In other words, if the issue is “our Wi-Fi sucks”, or general wireless malaise, then doing a wireless survey is most appropriate. If the issue is with a specific device, application, or set of devices, I may focus on packet captures to see what specifically is going on with those devices or applications.
For more on performing wireless packet captures see my YouTube channel.